Our computers are at risk again, and this time a simple one would suffice image, as a logo, to overcome the systems of check And safety (read also: is an antivirus or antimalware better?).
The worst news? Which is performed in BIOS and for this reason antiviruses or even reinstalling the operating system are useless: here is the vulnerability LogoFAIL. Let’s see how works and how defend ourselves.
Discovered by cybersecurity researchers at Binary, who showed their research at the conference for hackers “ethical” Blackhat Europe, LogoFAIL encompasses a series of security vulnerabilities which affect various libraries image analysis used in system firmware by various manufacturers during the device boot process.
In practice an attacker can exploit a simple image files as a logo (hence the name of the vulnerability) in PNG or BMP format to insert malicious code during computer startup.
And take control of it at a system level.
But how do they get there? According to researchers directly from system partition EFI (ESP) or within unsigned sections of a update of the firmware.
When these images are scanned during boot, the vulnerability can be triggered and an attacker-controlled payload can be executed arbitrarily to hijack the execution flow. At this point, researchers have proven that it can bypass security features such as Secure Bootincluding hardware-based verified boot mechanisms (such as Intel Boot Guard, AMD Hardware-Validated Boot, or ARM TrustZone-based Secure Boot).
These are the vulnerabilities discovered:
- CVE-2023-40238: Affects BmpDecoderDxe in Insyde InsydeH2O for some Lenovo devices. Caused due to a full signature error related to PixelHeight and PixelWidth in RLE4/RLE8 compression.
- CVE-2023-39539: Affects AMI AptioV and leads to a vulnerability in BIOS, where a user can cause unrestricted loading of a PNG logo file with a maliciously crafted type via local access.
- CVE-2023-39538: Similar to CVE-2023-39539, this vulnerability is also found in the BIOS of AMI AptioV. Allows a user to cause unrestricted loading of a BMP Logo file with a maliciously crafted type from local access.
Below you can see the mechanism of action of LogoFAIL, which can be simplified into three steps: introducing the logo into the system, starting the computer, running the code.
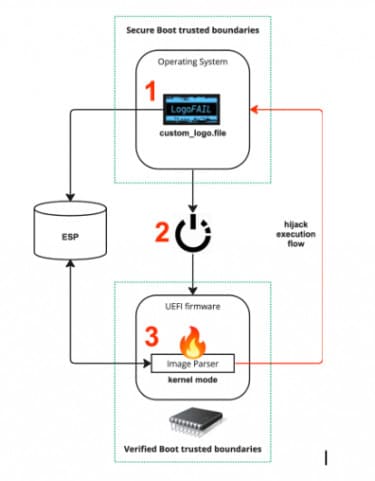
Source: Binarly
LogoFAIL it is particularly dangerous because it lives in the BIOS, so it survives one reinstallation of the operating system and bypasses most defenses as these tend to run and monitor operating system functionality and not code BIOS And UEFI.
One of the most important findings is that LogoFAIL It is not specific to the processor type and may impact processor-based devices x86 And ARM. Instead, LogoFAIL is UEFI and IBV (Independent BIOS vendor) specific due to the specifications of the parsers Of Images vulnerable that have been used.
This means that it has an impact not on a single supplier but across the entire ecosystem, and all three major IBVs are affected: AMI, Inside And Phoenix.
Binarly researchers said they remained shocked from their findings and the ease with which security technologies can be bypassed during boot, and how these vulnerability can open doors to potential attackers.
Overall, LogoFAIL should be considered much more dangerous of the recent bootkit BlackLotusfrom which it differs because it does not modify the bootloader, and intervenes after all integrity checks have occurred.
But which ones computer are they affected? At the moment there is not a complete list, but they certainly are hundreds of modelsincluding Lenovo, Acer and Intel.
What to do? Since there isn’t one yet list of affected computers, you need to check the manufacturer’s website if any updates or information have been released in this regard. Several manufacturers have issued warnings, such as AMI, Inside And Lenovoand if an update has been released you need to update The BIOS, something that unfortunately not everyone does or knows how to do.
Binarly has not defined precise examples of how this vulnerability can be exploited (and if it has already been actively exploited), but the general rules for protecting your computer should minimize the risks of infection.
In any case, keep in mind that if your computer behaves in strange way and you think it was infected by a malware but reinstalling the system doesn’t fix the problem, you may be a victim of this exploit.
Binarly