how to protect yourself” title=”This email opens the doors of an attacker to your Instagram account: how to protect yourself”>
We always invite you to use these pages two-factor authentication (or better yet the passkeys) to protect your accounts, but what to do if we also deliver the second one authentication code to an attacker?
This is what happens with the phishing, a type of attack computer scientist that pushes us to reveal ours login data to someone who pretends to be from the customer service of a platform, and who is currently being used in a very elaborate way to enter our account Instagram (do you know what the difference is between antivirus and antimalware?).
This is what the cybersecurity company discovered Trustwave, who published the mechanism of action of the attack and how to defend oneself, or at least how become suspicious.
Just to understand what is happening, to increase the security of your Instagram account, the platform allows you to set up two-factor authentication, i.e. a code to be entered at each new login.
This code can be created from an app like Google Authenticator or Microsoft Authenticator, sent via SMS or even from WhatsApp, but to be more secure, Instagram also offers you a series of backup codesfive 8-digit numbers that can only be used once and that you can print or save to be able to access your account also without phone.
And these codes are the object of desire of the phishing campaign we are talking about, because they allow you to bypass other phone-based authentication methods.
But how does aggression work? It all starts from a seemingly innocuous thing e-mail (and here you should become suspicious, but let’s see why later), which, in its graphics and contents, passes itself off as coming from Half and with tones alarmist warns you that your account is “violating copyrights“.
The message creates a sense of urgency with a message alerting you that you need to submit a appeal within 12 hours, under penalty of deletion of the account.
And what does an unaware, scared user do? Click on links, a button named “Go to the appeal form“.
Trustwave notes that this link does not point to Meta, but contains a connection for Google notifications (second alarm bell).
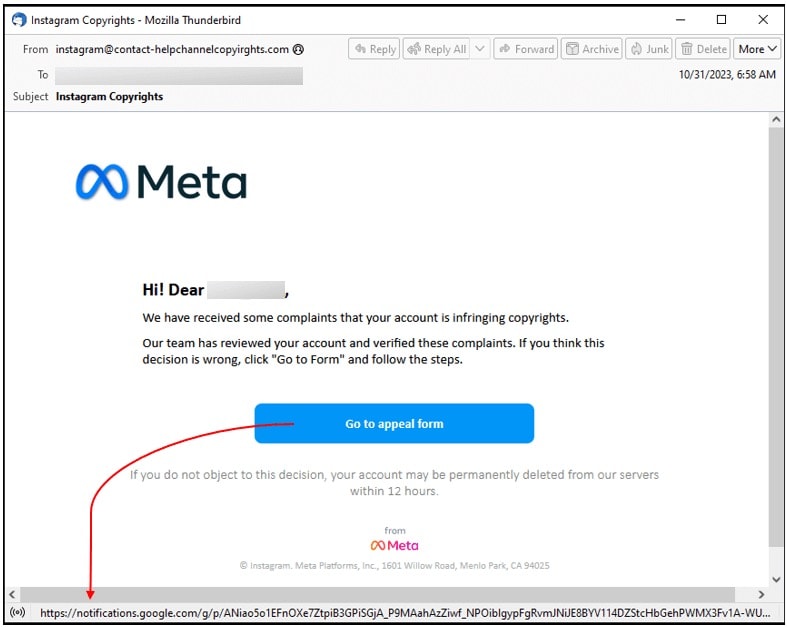
Phishing emails. Source: Trustwave
After clicking on button, the user is redirected to a site that mimics the Meta page very effectively, but which is hosted on Bio Sites, the landing page quick setup Squarespace (third alarm bell: you are not on the site Half!).
Why Bio Sites and Google Notifications Link? Probably to avoid detection give them spam tools of Gmail (or your provider) and track clicks.
At this point if the user clicks on the button Go to the confirmation form (Confirm my account) (Go to confirmation form), you will be directed to phishing site real, created to collect your data (again, not Meta: fourth alarm bell, you should always look at the address field of the browser).
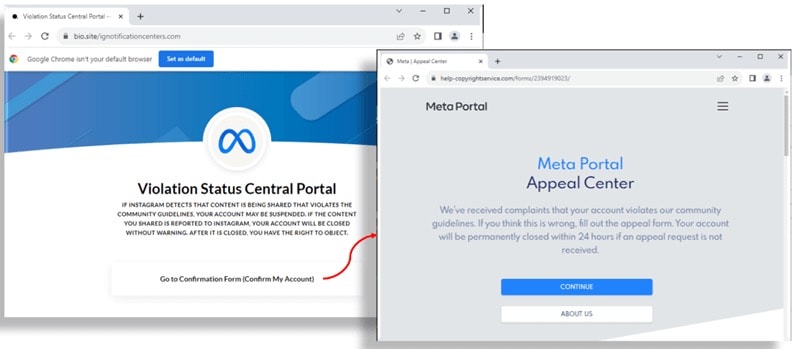
Two fake Meta sites. The first hosted on Bio Sites and the second, on the left, to collect your data. Source: Trustwave
Now the login credentialsemail and password (twice), and after providing them you will be asked if it has been enabled two-factor authentication (2FA).
By clicking Yes, you will be asked for one of the five backup codes of Instagram generated by the user, and just for greater security you will also be asked to enter the address e-mail and telephone number.
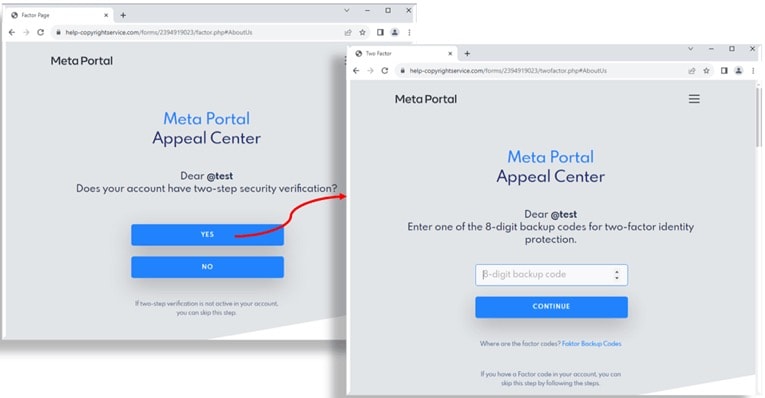
Two-factor authentication code request. Source: Trustwave
Your login data will be collected, and attackers will be able to enter in your Instagram account of the victim, potentially even changing the password and excluding it from your own accounts.
How to defend yourself? As we have seen, there are several alarm bells that should make us suspicious, but the first is the sender of the email. If you look at the email address the request came from, you will see that it is contact-helpchannelcopyrights[.]comwhich has nothing to do with Half.
And the same goes for the addresses of the various ones connections. As you can see, even very elaborate attacks like this have aspects that should make us suspicious.
In any case, try never to enter the sites by following the links offered, but if possible always insert yourself the address in the browserand never share passwords and passcodes outside of Instagram.
If you realize that you have given your login details to an attacker, immediately change your password and generate new backup codes by going to Instagram, then clicking on Settings & Privacy > Account Center > Password & Security > Two-Factor Authentication > [Il tuo account Instagram] > Additional Methods > Backup Codes > Get New Codes.
There is another aspect: up Bio.site Trustwave found several sites pretending to be from Meta, and noted that while some no longer link to active phishing sites, others are constantly being updated, suggesting that bad actors continue to improve their “traps.”
Trustwave